I had a lot of fun writing this one. Palo Alto Networks is a company I’ve admired for a long time; it’s the world’s biggest standalone security company, has an arm in virtually every category of cyber, and is an active acquirer of dozens of pioneering startups. So I thought it was important to peer into the company’s history, understand how it’s managed to innovate over the last 18 years (an eternity, in cyber years!), and explore where it might go next.
If you’re curious about security, cloud infrastructure, or AI/ML, join thousands of others and subscribe! This is a long one, so please open outside of your email client.
Overview
In this piece, my friend & cybersecurity analyst Francis (subscribe to his Substack here!) and I dissect the rise of Palo Alto Networks (PANW). We begin with a history of the company, expand through their core products, and provide commentary on the road ahead as they race to become the world’s first $100B security company. We see great opportunity for Palo Alto Networks in doubling down on cloud and application security, expanding to identity authorization and permissions, and deepening their endpoint protection portfolio.
PANW is the world’s biggest standalone security company, generating $6.1B in revenue, supporting over 80k customers, and wielding a $56B market capitalization. The iconic business was built on a next-generation firewall that disrupted incumbents Checkpoint and Juniper Networks over the last two decades. Today, Palo Alto Networks competes in three markets: network security (Strata & Prisma SASE), cloud security (Prisma Cloud), and security operations (Cortex). PANW's moat is in its unified control plane across hardware & software, and broad coverage of the network, security operations center, apps, and cloud.
Palo Alto Networks estimates its TAM to be $110B growing at a 14% CAGR and projects $8B in annual revenues by FY 2024E. The company expects 23% forward growth, blended across the original firewall business and the “next-gen security” business, comprised of Cortex and Prisma Cloud. The latter two products, at a $2B run rate and growing by 60% YoY, are key to landing a new generation of customers. PANW is now recognized in 13 categories by industry research firms like Gartner, up from 9 in 2020. As the macro environment forces companies to focus on total cost of ownership, PANW’s product suite and geographic diversity are going to be two pillars of strength.
Palo Alto Networks’ is one of the greatest examples of M&A integration in cybersecurity and perhaps even in software broadly, after spending over $4 billion on 17 companies forming its Cortex and Prisma Cloud business. The biggest question facing the company is if they can successfully integrate all these 17-companies over the next 3-5 years and upsell their new products to their existing 60,000 firewall customers.
Founders building the next generation of cybersecurity could learn from the three tenets of Palo Alto Networks’ strategy for achieving dominance: deliver value quickly, secure tomorrow’s architecture, and strategically consider in-organic growth with M&A and partnerships.
Founding Story
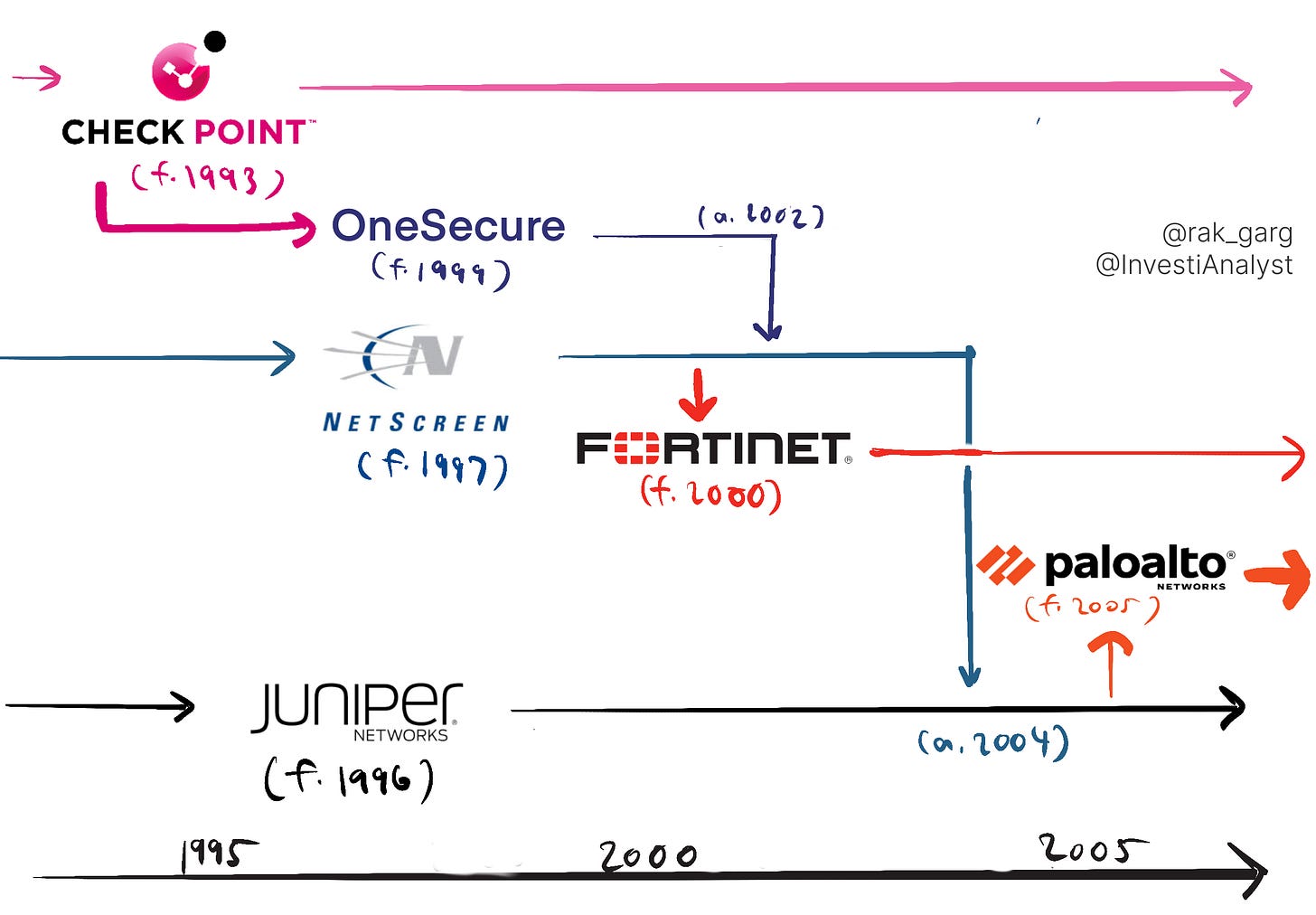
The longest tenured employee at Palo Alto Networks is Nir Zuk, the company’s founder and CTO. Zuk was a founding engineer at incumbent Check Point, previously the world’s biggest security company until it was de-throned by Palo Alto Networks in 2014. Check Point, in many ways, created the modern enterprise security market and seeded the industry in Tel Aviv, by successfully commercializing an idea borne a decade earlier, by Digital Equipment Corporation (DEC) in Boston.
In the 1980s, DEC created the world’s first firewall. The product was innovative, yet unviable; it’s stateless design meant it couldn’t contextualize network traffic and would block safe packets. Gil Schwed, graduate of Israel’s legendary Unit 8200, saw an opportunity to build a new kind of network firewall—one that could block packets based on their context. Schwed started Check Point in 1993 around the hypothesis that stateful inspection could unlock firewall efficacy. Security teams could own and operate a stateful firewall without any help from IT since it was self-contained, and they’d stick around because Check Point’s administration console was the most delightful experience on the market. Thirty years later, stateful inspection still underpins all major network security products, the best security tools still prioritize ease of adoption, and user delight is still a critical axis of competition.

Zuk stayed at Check Point for five years before leaving in 1999 after believing R&D at the company had ossified. He started OneSecure, the first intrusion prevention system, that sat behind the firewall and ensured that any packets let through weren’t malicious. In 2002, OneSecure was acquired by firewall appliance vendor NetScreen, founded by Ken Xie who had recently left to start Fortinet. The latter, along with Check Point, are Palo Alto’s greatest rivals in the firewall business. Side note: Zuk’s co-founder at OneSecure, Rakesh Loonkan, would go on to found Transmit Security, which raised a $543m series A at a $2.7B valuation in 2021. NetScreen was acquired by Juniper Networks in 2004.
Zuk quickly left the dot-com darling after feeling a familiar frustration over R&D agility. Three insights led to the founding of Palo Alto Networks in 2005. First, Zuk anticipated a growing need for network security as application complexity and network consumption grew monotonically. Second, virtualization (evangelized by then mid-stage startup VMWare) was changing how applications communicated; software-defined networking was going to take over, and firewalls needed to protect virtual and eventually containerized apps differently from traditional apps. Finally, the “box” business that Juniper and Cisco had made their bread and butter would eventually saturate, and software would become the critical differentiator.
The Platform Journey
Palo Alto Networks found product market fit with its initial firewall product before expanding into security operations (SecOps, SOC) and eventually cloud security. The company would find the transition from product to platform an initially challenging one, with early acquisitions between 2014-2018 failing to meaningfully increase market share in new categories. Today, PANW offers 23+ products across the three categories of network, SecOps, and cloud, and offers unified threat management and administration across each of those surface areas.
A. Network Security Platform (2005-Present)
When the company started, networks defined the enterprise perimeter. Securing the network was consequently the highest-value place to be. Over the ensuing decades, the network perimeter dissolved with remote work and cloud distributed applications. Palo Alto’s firewall products, once 90%+ of revenue, still comprise 60%+ of the business today. We expect revenue share to decrease as the company scales its Prisma SASE offering, delivering network security over the cloud rather than via a firewall, and invests in new products.
Firewall
Firewalls traditionally execute rules based on a packet’s source and destination IP addresses, the network protocol in use, and the ports being accessed. New attacks in the early 2000s, like SQL injection and XSS, would fly by undetected. Zuk’s startup OneSecure had pioneered intrusion prevention (IPS), which would catch packets that had made it past the firewall based on statistical anomaly detection of whether a packet was likely to be safe or not. Static firewall rules were unequipped to handle the modern application demands of contemporary workforces, and deeper context was needed into application behavior.
PANW’s early product was a tight coupling of firewall, IPS, and VPN. Over the next few years, the company added deep packet inspection, sandboxing, and URL filtering. The most meaningful innovation here was App-ID, which provided greater visibility into which applications were communicating on the network, and more fine-grained control over those applications’ behaviors. The complete package was dubbed Next-Gen Firewall (NGFW). Even as the world realized the user, not the network, defines the perimeter, PANW capitalized on App-ID to dominate zero trust network access (ZTNA). Application awareness provided a level of visibility competitors couldn’t easily match and was a real technical moat for a few years. PANW’s understanding of containerization provided additional edge, in that the NGFW could be deployed physically on an appliance, virtually, in a container, or via cloud.
The firewalls were so far ahead of the market, they retained dominance for a decade. According to a Hhhypergrowth report on Palo Alto:
“Palo Alto…quickly became the leader in Gartner's Magic Quadrant in Enterprise Network Firewalls that debuted in 2011, disrupting the market ruled by network security giants like Juniper, Cisco, and SonicWall – as well as leap over the more recent upstarts like Fortinet (founded in 2000) and Barracuda (founded in 2003).”

Prisma SASE: Access and SD-WAN
Network security infrastructure has since evolved from deployments in data centers to hybrid access via the cloud. Companies used to buy and administer physical networks with switches, routers, appliances, wireless access points, and VPNs, trying to ensure that all employee traffic was on a trusted network. Two recent shifts have dissolved this paradigm:
Modern applications began appealing to users directly through product-led growth. IT and security saw dwindling visibility into what tools were actually in use in the enterprise.
Remote work required the workforce to communicate on insecure networks at home, in cafes, and from various Airbnbs during that period in 2020 when everybody in tech suddenly became nomadic.
Palo Alto’s core firewall business had developed solutions for zero-trust network access (ZTNA), including secure web gateway (SWG) and VPN, but this only worked as long as requests were actually routed through the firewall, SWG, or VPN. Latency caused by these central choke points was untenable.
Zscaler (f. 2007) and Netskope (f. 2012) had created SASE (secure access service edge) platforms where enterprises would deploy and secure networks in the cloud, in geo-replicated and distributed topologies. PANW launched its contender, Prisma Access, in 2021. The product was powered by App-ID and offered access control at a sub-application level. Network access could be revoked automatically in real-time as app behavior became anomalous, and worked across both the network- and application-layer.
As of PANW’s most recent quarter, Prisma Access has grown to over $1B in bookings while maintaining a 50% ARR growth rate. SASE is a land product, with nearly a third of Prisma Access customers being new to Palo Alto Networks. As enterprise networks sublimate to the cloud, we expect firewall TAM to stagnate, while adoption of SASE products like Prisma Access accelerates over time.
B. Cortex: Security Analytics Platform (2014-Present)
Early Platform Attempt
In 2014, PANW generated $598M in revenue, growing 51% YoY, had $650M+ of cash on the balance sheet, and a 73% gross margin (imagine that, for a business selling physical firewall appliances where 43% of revenue is services!). In more technical terms, the core business was ripping, but the NGFW market was getting increasingly competitive, and the company was looking for other high-margin sources of subscription revenue.
Cue the push into becoming a security analytics and intelligence platform. From PANW’s 2014 10-K:
Our enterprise security platform consists of three major elements: our Next-Generation Firewall (NGFW), our Advanced Endpoint Protection (AEP), and our Threat Intelligence Cloud (TIC). Our Next-Generation Firewall delivers application, user, and content visibility and control ... Our Advanced Endpoint Protection, which we expect to release in fiscal 2015, prevents cyber attacks … [on] endpoints. Our Threat Intelligence Cloud provides central intelligence capabilities as well as automated delivery of preventative measures.
The company makes its first four acquisitions over the next three years, which were ostensibly aligned to the endpoint and workload security categories based on their product descriptions:
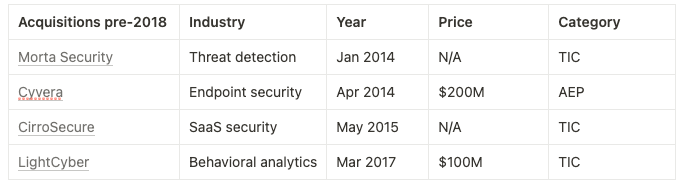
Directionally, the 2014 strategy was correct. Endpoint security, e.g. securing the activity and data on phones, laptops, and any other user devices, is one of the largest markets in cyber, and throws off immense amounts of data exhaust. Crunching all of that data, along with logs from other products like network appliances and firewalls, would lead to security analytics becoming a gigantic market. Incumbent Splunk hit a then-all-time high market cap of $15B that year!
The miscalculation was the speed at which the cloud would start to dominate enterprise workloads, and the flexibility of cloud data warehouses. While PANW was doubling down on traditional threat intelligence and response across the traditional vectors (network, endpoint, and SaaS), the cloud wars had already been raging for years. AWS was a household name in the valley, having had a decade by 2016 to mature the S3, SQS, and EC2 services that would underpin its cloud for the next ten years of software development. Google and Microsoft had entered the fray with compute and storage offerings, and DigitalOcean was dominating the hobbyist and SMB markets. PANW wasn’t just late to the cloud train, the company was at serious risk of missing it entirely.
Growth slowed from 51% in 2014 to 28% in 2017. Enter Nikesh Arora as CEO in 2018, who cut his teeth as the CMO of T-Mobile (differentiating the carrier in a commoditizing telco industry) and CBO of Google (grew search from $2b to $60b in annual revenue). In his first letter to stockholders, Arora writes:
Since becoming CEO in June, I have talked with more than 100 customers, partners, and experts…[and have] come away with several observations: the security market is large and growing; the need for security transformation is undeniable; and we have a tremendous market opportunity ahead, as analytics and a more simplified way of consuming cybersecurity become core to the success of every business. The transition to be viewed as more than just the network security leader to the global leader of cybersecurity is going to be intense.
And intense it was. To exit the interregnum, Arora would spend nearly $4B over his first four years as CEO buying the future: $2B for a new set of cloud-native security operations products that were combined with older acquisitions and became the Cortex platform, and $2B for the startups that would become the Prisma cloud security platform. This was strategic; building cloud capability in-house would take a long time and divert resources away from the core network security business, so M&A was an effective lever to effectively outsource R&D to the startup landscape.
Post-Nikesh Arora Cortex Platform
🧠 Cortex aspires to modernize and automate as much of the security operations center (SOC) as possible, from the endpoint, across the network, to the SIEM where it’s all eventually stored. Products include:
XDR: extended detection and response (XDR) and endpoint protection (EPP/EDR)
Data Lake: security information and event management (SIEM)
XSOAR: security orchestration automation and response (SOAR),
XPANSE: external attack surface management (EASM)
XSIAM: SIEM + SOAR that enables autonomous security operations powered by AI/ML.
Over a series of acquisitions, Cortex has grown from the original threat intelligence focused offering to span several areas in cloud-native security operations and analytics:
Cortex XDR: Extended Detection and Response
PANW first entered endpoint protection in March 2014 after acquiring Cyvera, which was integrated with WildFire malware detection and later bundled into TRAPS (Targeted Remote Attack Prevention System). They also acquired LightCyber in Feb 2017 for signature-based behavioral analytics. These were misses; malware detection & anti-virus were seen as perfunctory, and signature-based platforms were passé.
Endpoint protection was being reinvented in the cloud, and Crowdstrike’s Falcon was taking off. PANW responded with an acquisition of SecDo in 2018, adding EDR to their Traps EPP. A month later, Zuk coined the term XDR at PANW’s Ignite conference, expanding Traps into a more holistic EDR solution, with an ML-driven detection engine over NDR (network), CDR (cloud infrastructure), and UEBA (behavioral analytics). Despite these efforts, PANW still lags the major endpoint security players according to the latest Dec 2022 Gartner report on EDR.
Cortex Data Lake
Having a stream of data from endpoints and a view of your organization’s assets is useful, but very hard to make any sense of. Snowflake has done a tremendous job over the last few years capitalizing on security; it turns out, an analytical data store capable of handling mind-bending scale is pretty well suited to security use cases! AWS, Azure, and GCP picked up on this and launched their own security data lakes, augmented with security integrations. Historically, before data lakes, these systems were security-specific, operated in silos, and dominated by Splunk.
PANW’s data lake ingests data from cloud posture management tools, firewall logs, identity logs, third-party platforms, cloud environments, user behavioral analytics, and forensics tools. Each of these vectors is, unsurprisingly, an existing asset in PANW’s product portfolio. The data must be normalized (read: transformed, in modern data stack lingo) and stored for compliance, analysis, and SOAR automation.

XPANSE: Attack Surface Management (ASM)
Endpoint coverage is table-stakes, but doesn’t protect you against attacks on your infrastructure. Not anymore, anyways. In an on-prem world, you could (sort of) view a server as an endpoint. In a cloud world, short-lived containers, distributed networks & delivery fabrics, and new cloud resources deployed at will cannot be managed by an EDR solution.
An outside-looking-in solution is needed. CISOs want to see what malicious actors see: a view of the enterprise from the outside, with weaknesses highlighted. The 2020 acquisition of Expanse, PANW’s most expensive to date, brought asset tracking across on-prem and cloud to the platform, helping security teams map and manage their attack surface.
XSOAR: Security Orchestration, Automation, and Response (SOAR)
Realistically, many of the alerts generated by security tools are false positives, many are easily remediated but take manual work, and only a few require close examination and response. Gartner coined the term SOAR in 2015, after seeing Phantom (acq. Splunk) and Demisto (acq. PANW) gain footing with security analysts for running scripts and workflows for automatic remediation. Demisto, at $560M, is PANW’s second largest acquisition to date and still the largest outcome in the category. Demisto combines SOAR, incident management, and investigation to help security operations teams respond and remediate common alerts automatically. Demisto was rebranded to Cortex XSOAR, which was announced in early February 2020.
XSIAM: Autonomous Security
The average security operations center (SOC) receives over 11,000 alerts a day, and proliferation of enterprise apps and security point products is only exacerbating alert fatigue. SOC analysts are strapped for time and resources, leading to ignored alerts at worst, and weeks-long investigation times at best. SOAR solves some of these problems, but still needs someone to anticipate and create workflows. XSIAM (extended security intelligence & automation management) innovates on SOAR by proactively detecting problems, creating remediation plays, and executing them as needed. The platform launched in Feb 2022 and expanded to identity threats last month. In Zuk’s words, SIEMs are human-driven while XSIAM is ML-driven, integrating threat intel over the entire customer base similar to CrowdStrike's ThreatGraph.
Palo Alto is well primed to deliver on this vision, given their ownership of the endpoint and network, understanding of common attack surfaces, and data lake that ingests and normalizes signals from each surface. No other vendor, except Microsoft and Crowdstrike given their breadth of offerings in endpoint and ML (see Appendix), can reasonably compete in this category.

MDR: Managed Detection and Response Services
Finally, the reality is, most businesses don’t have a security operations team. Even if they do, they might want a blanket of security experts monitoring their environments 24/7. PANW acquired Crypsis in August 2020 to add incident response and forensics consulting services to its XDR platform, competing against similar services from Mandiant (acq. Google, $5B in 2022) and CrowdStrike’s MDR service. The 150 security consultants from Crypsis were merged with PANW’s existing threat intel specialists into a new unit: Unit 42, which businesses subscribe to for MDR and security expertise.
C. Prisma: Cloud Security Platform (2018-Present)
The cloud didn’t just disrupt the networks or security analytics, it created entirely new attack vectors that traditional security products couldn’t protect against. For one, the cloud enabled huge velocity gains in development organizations, allowing engineers to dynamically access whatever resources needed. The downside is cloud sprawl and infrastructure insecurity that security teams have very little visibility into. Any permutation of these vulnerabilities and resources could become a new attack path.
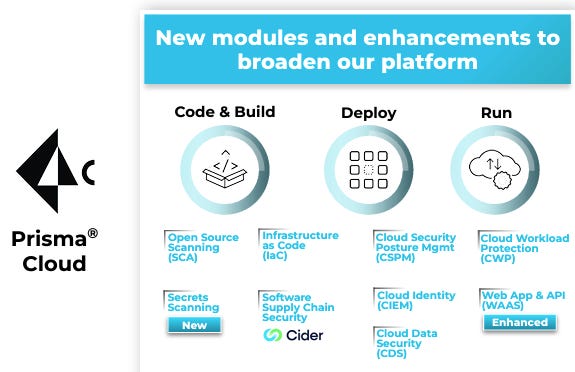
💎 Palo Alto has strived to get closer to the engineer with Prisma, a code-to-runtime cloud native application protection platform (CNAPP). Prisma Cloud delivers cloud security posture management (CSPM), cloud workload protection platform (CWPP), cloud network security, and cloud infrastructure entitlement management (CIEM) capabilities. The products include:
Prisma Cloud - CSPM, CWP, CIEM, API Security, Data Security, WAF
Prisma Access - SASE, ZTNA
Prisma Code Security - Supply chain security, application security
To create Prisma, the company made the following acquisitions over the last several years
Cloud security posture management (CSPM)
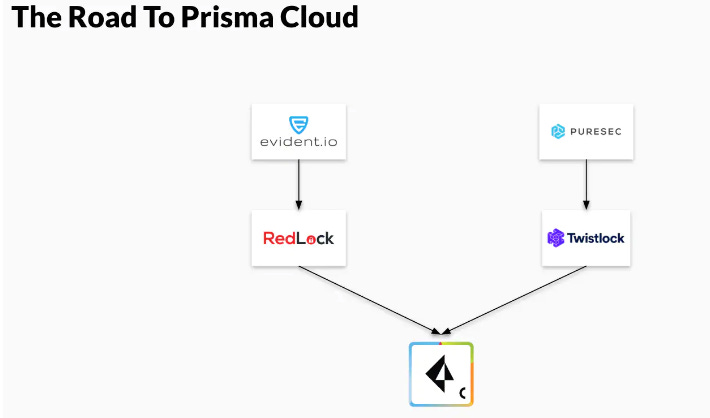
The Prisma platform began with Prisma Cloud, a CSPM tool resulting from the 2018 acquisitions of Evident (disclosure: a BCV company) and Redlock. PANW already had inline security through the NGFW, but needed to secure companies building internal services and products on the cloud. Evident had strong IaaS, API, and host-based protections, allowing customers to check for compliance, manage cloud storage settings, and ensure proper configuration of all cloud services. The majority of cloud breaches still happen because one or more of the myriad services in use at a company are misconfigured, so catching these misconfigurations as quickly as possible is critical.
Serverless and Container
Like cloud services, container environments can also be misconfigured, leading to runtime security and reliability issues. Modern apps are increasingly built on containers as a default. PANW added container runtime security through the acquisition of Twistlock, enabling monitoring for Linux, Docker, and Kubernetes, visibility into environment configuration, and preventive remediation before deployment. PureSec was acquired to provide security for serverless functions, which many believe to be the future of cloud compute delivery, and Aporeto for workload identity which allows machines to trust API calls and compute requests from third-parties or restrict access to networks and data accordingly.
Supply Chain, DevSecOps, and Application Security
By 2021, the company would begin realizing the importance of developer security. To stop attacks from happening in the first place, developers must ensure application code is secure, and that secrets (API keys, tokens, etc) stay secrets. The acquisition of Bridgecrew brought PANW closer to the developer, enabling engineers to use an infrastructure as code (IaC) scanner to detect and fix security issues during infra deployment. Bridgecrew also provided security assessment and enforcement capabilities throughout the DevOps process. According to PANW’s Q1 2023 earnings call:
“IAC became our ninth integrated module of Prisma Cloud at the end of January. And in the first 6 months of availability, we already have over 200 customers, making it our fastest-growing new module.”
Shifting further left into the software supply-chain, PANW acquired Cider Security, giving the platform visibility across the CI/CD pipeline, Software Composition Analysis, and Secret Scanning. The product competes squarely against Snyk and a long-tail of supply chain security companies.
Cloud Native Application Protection Platform (CNAPP)
Today, Prisma Cloud provides a comprehensive suite of cloud security products from code to run-time, achieving most of Gartner’s requirements for CNAPP. Palo Alto’s cloud coverage positions them to ride cloud security tailwinds from over $500B in public cloud spend. The company still mostly provides an agented solution for cloud security, so it’s possible they develop or acquire an agentless solution to bolster their go-to-market and deployment. Prisma Cloud will continue to be a critical growth driver for Palo Alto, facing competition from upstarts like Wiz ($10b valuation) and stalwarts like ZScaler and Check Point.
The Race to Become the First $100B Security Company (2023 onward)
Every cybersecurity observer wants to know: who will become the first $100B cybersecurity company? As of February 2023, Palo Alto Networks had a market cap of $56B, making it the world’s most valuable security company. Long-time rival Fortinet is a close second at $46B market cap and there are a long tail of public decacorns like Crowdstrike, Cloudflare, and Zscaler which are investing in their own platforms. The first $100B security company will have to be well-positioned in tomorrow’s most important security markets, leverage consolidation dynamics, expand market share, and execute like hell.
Positioning in tomorrow’s markets
Gartner observes that cloud and application security are the fastest growing categories in security. They project that 65% of enterprises will have consolidated networks behind SASE, up from 15% in 2021. Prisma Cloud and Cortex are respectively positioned in the right categories of AppSec and XDR for supporting security operations teams. Our conversations with security leaders and platform teams confirm that these areas are dramatically underserved today.
Expand Market Share and Consolidate
In recent interviews, Arora has stated that Palo Alto’s market share increased from 1.5% to 3% between 2018 to 2022, despite having over 80K customers and $6B in revenue. This underscores two points about cyber: the industry is 1) gigantic, and 2) ultra fragmented. Budget decisions are under more scrutiny and automation is a top priority, reducing appetite for point products. Palo Alto stands to benefit given existing relationships with large enterprises and their continued expansion of the Cortex and Prisma platforms. Channel partnerships through NextWave and a rebel alliance GTM pushing Cortex and NGFW through AWS and GCP marketplaces provides ammunition against Microsoft. Consolidation of niche players, landing modern companies (e.g. is Notion a PANW customer?), and expanding within enterprise stalwarts will be critical.
Expansion Areas
To become the first $100B security company, PANW will have to expand their platform to cover more cybersecurity surface area with new attack vectors and deepened existing coverage. Identity, Endpoint, and Apps provide interesting potential avenues where they could close the gap.

Identity; Identity remains a core pillar of enterprise security. Okta is trying to secure a moat with Okta workflows, which XDR/SOAR vendors are well positioned to compete with if they add IT and HR integrations. Identity has become the new perimeter, becoming a critical upstream data provider for SIEM-based detection and SASE-based networking. Palo Alto currently has endpoint that protect the device/workload and SASE coverage through Cortex and Prisma, so owning authZ with IGA/PAM/IAM could be easy avenues for revenue generation.
Browser isolation; This would be a logical add-on for existing endpoint protection or SASE customers, and the technical barrier to entry has plummeted with Chromium-based browser architecture. Cloudflare, Zscaler, Island, and Talon are existing solutions, but Prisma Access provides an easy distribution channel to defend against incumbents and upstarts. The browser also opens the door to anti-phishing protection, allowing PANW to access bigger endpoint security budgets.
Supply chain security; Cider acquisition suggests PANW has bigger plans in developer life-cycle security, and none of PANW’s primary competitors are adequately equipped yet. There is a critical window of time to become the developer security platform, which we’ve written about before. [Link to 2023 predictions doc/Link to Appendix]
Challenges Ahead
Acquisitions are hard to stitch together. Palo Alto has done a good job acquiring leading venture-backed companies at early stages. To PANW’s credit, many early founders have decided to stay at the company. However, integrating technology, people and process across 17 companies within four years can be challenging. Technology integrations across different stacks, pricing and billing systems, and cultural differences can get messy at the scale phase. On the flip side, new acquisitions bring new cultures and new hunger to the organization, creating resiliency and preventing tunnel vision. A key part to PANW’s success will highly depend on their ability to integrate all their product solutions to customers.
Competition: Microsoft just announced their security business has crossed over $20B in ARR. The vendor lock-in argument breaks down when lock-in produces real value, like Microsoft’s AI/ML driven XDR tooling that learns from the industry’s largest corpus of real-time signals and events. That, along with the ability to sell data storage at scale discount, gives Microsoft a strong advantage in security. Fortinet continues to be a dominant presence in SD-WAN, NGFW and OT security. Zscaler leads on the SASE front, and Crowdstrike has a lead in endpoint security. PANW will need to show strong product differentiation while creating space between itself and these companies. See full product comparison in the Appendix below for more details.
Lessons for Security Founders
Deliver value quickly
Check Point was able to build a meaningful business in firewall when DEC failed, because its product could be procured, owned, deployed, and administered by a single buyer and user: the security team! Network operations teams no longer had to get involved in rolling out and testing firewall products. Palo Alto Networks delivered value quickly with new deployment models (e.g. firewall as a service, containerized firewall, etc) and retained users with greater context into application behavior, which Check Point couldn’t easily compete with. . Delivering value quickly is a necessary pre-requisite to building a meaningful security product.
Pay attention to tomorrow’s architecture
Palo Alto Networks disrupted Check Point by acting on a shift in the way applications were built and deployed, namely on virtual machines, then in containers, and finally on the cloud. In 2005, none of these things were obvious. VMWare was a mid-stage startup, and Docker wouldn’t exist for another eight years! Security entrepreneurs today can either secure the same areas better than anyone else, or secure new surface areas. Some potential areas for innovation include ML model security, eBPF-based runtime monitoring, and anti-phishing outside of email. We encourage entrepreneurs to consider how tomorrow’s F500, which are leading mid-stage startups today, create and deploy their applications, and build for the security implications of those architectures.
Consider in-organic growth
If you’re a well capitalized startup and post-product market fit, consider acquisitions as a lever to bolster your platform faster, and more comprehensively, than in-house R&D can. Focus on how quickly you can integrate new technology and what the acquisition buys you strategically (e.g. access to new customers, new threat vectors, or new talent). If there are natural synergies between your core product (like Palo Alto’s NGFW) and the target company, buying can make sense. Palo Alto was a company wallowing in the commoditizing world of firewall security world it helped create. Prisma Cloud was a struggling product by the end of 2017. PANW used cash on their balance sheet to acquire and bundle new products into Prisma Cloud. At the December 2022 Ignite event, Arora proudly stated that:
“Across the board, we probably spent $4 billion on about 17 companies since I’ve been here. And I’d say most of them are working. Forty percent of companies are a net new capability that didn’t require integration, 60% require integration. And we had a common theme … to buy the No. 1 or 2 in the industry.”
Nir Zuk has experienced the negative impacts of acquisition twice, where once nimble startups became encumbered by the political and technical overhang of the parent company. These experiences have enabled him and Arora to innovate on M&A integration, with the mothership adopting the startup’s agility and culture rather than the other way around.
Leadership and Notable Alumni
Palo Alto Networks and Check Point before it have dominated cyber security for basically as long as the industry has been around. Some of the most innovative security startups have come out of these two companies, with a select few shown below.
Appendix: Feature Comparison
Crowdstrike, Zscaler, and Cloudflare have each built $20B+ businesses bringing the old categories of endpoint, network, and content delivery to the cloud. Microsoft generates that much in security revenue a year, with the most fully featured platform of any company we’ve seen.
.













I am a sucker for long reads and what a great read this was. Thanks Rak! I was part of the early journey of the company. Most folks don't know but PANW had laid off folks as the magic wasn't working until they figured out the unique GTM motion - don't sell firewall as a firewall but as an IPS... and the rest is well a $6B revenue story.
Crowdstrike.