Security's Fifth Estate: Predictions for 2023
Application security, automation, and AI-driven anti-phishing could spawn the next big security platform.
Thank you to my partner Enrique Salem for debate and feedback. If you’re thinking about security, I’d love to meet you. Shoot me a note at rgarg@baincapital.com!
Four Estates
Historically, there have been four big categories in security: cloud (evolving from networks prior), identity, email, and endpoint. In every generation, each of these categories has supported at least one really big winner.
Over the last decade, new threat vectors have illuminated gaps in the armor, leading to a proliferation of security point products. CISOs opted for best of breed tooling because, as everyone knows, you’d rather have paid up for a tool that works than have saved budget and gotten breached. Today, point product proliferation is reaching a tipping point. It’s common to hear CISOs lament the dozens of point products they have tried to no avail. One CISO I spoke had adopted over 50 startup products in his security program, and wasn’t sure that many were effective!
The security world is still in the midst of a shift left. Teams are hesitant to buy tools affecting (increasingly cloud-deployed) resources and applications without developer buy-in. Software engineers are taking on more work (reliability, QA, on-call rotations, testing, etc) with lower headcount, especially in today’s more capital-constrained environment.
At the same time, security teams are more technical, and more engineering-heavy, than their predecessors. Hybrid roles like security engineering and DevSecOps engineering are growing in popularity while security teams move away from traditional SOCs and analyst/operator roles. The buyers are getting smarter, faster, leaner, and gaining organizational capital. The builders must do the same.
This year, I’m looking for a fifth estate in security, and the answer might lie in a new breed of AppSec products, sophisticated AI-driven guardrails, and automation platforms.

Prediction #1: AppSec finally understands AppDev
In 2022, Okta, Github, and Microsoft were all breached, proving that supply chains, even at sophisticated organizations, are uncovered at worst and clumsily held together by bandaids at best. At the same time, there are dozens of point products targeting each stage of the software lifecycle. Virtually none, except maybe Snyk, have successfully expanded out of their original categories to become the developer security platform. There are three reasons why this is a tremendous opportunity:
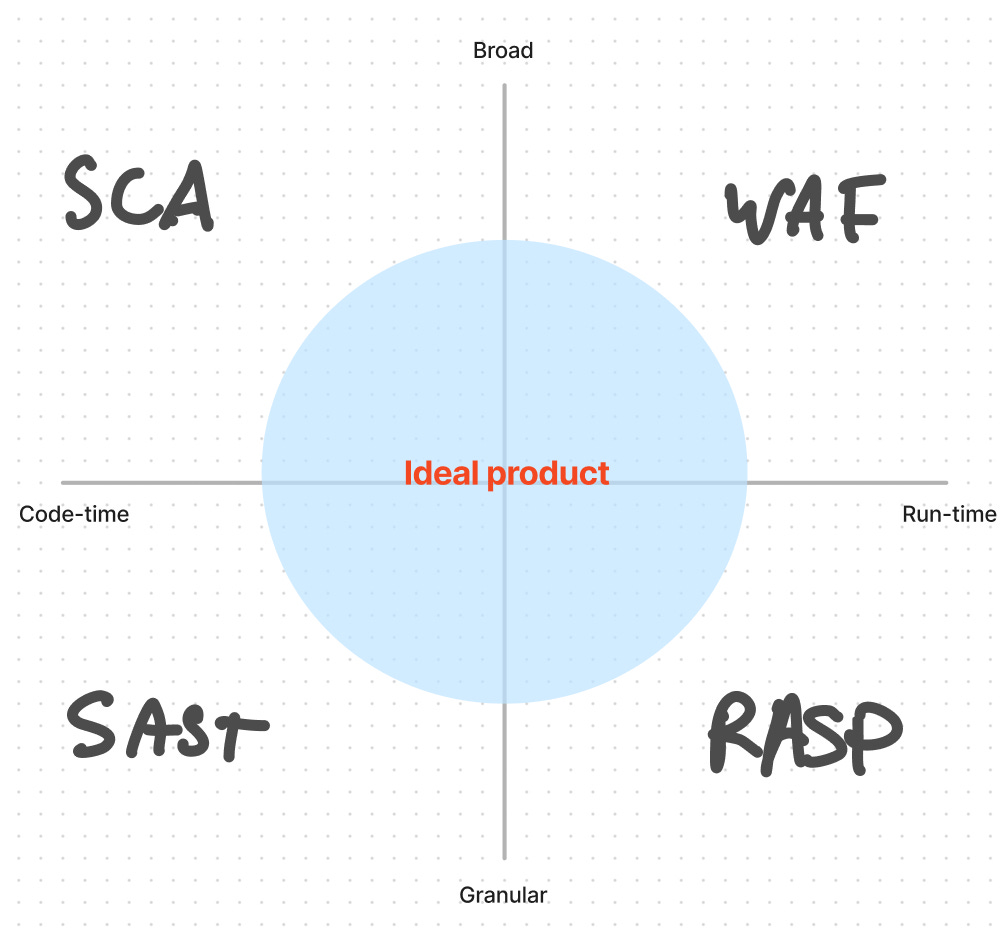
First, the old guard of AppSec is turning over. Old-school web application firewalls (WAFs) operate at the network perimeter, preventing known malicious requests from reaching apps. WAFs block known attacks like cross-site scripting and SQL injection, which is necessary, but insufficient to protect web apps today. WAFs quickly became a standard part of SASE and cloud platforms over the last five years, while perimeter porosity has increased. Runtime application security platforms (RASPs) are more granular, examining each step of app execution, but are tougher to deploy and result in too many false positives. A median approach is needed, one granular enough to have app-level context (like RASP), yet broad enough to be easy to deploy (like a WAF).
Second, there is no dominant platform unifying security alerting across both pre-deployment and at runtime. Correlating vulnerabilities across both stages helps engineers focus on problems that actually need fixing. The alternative is engineering teams drowning in hundreds of arbitrary Jira tickets each month generated by tools they didn’t even know existed! (Word to the wise: auto-creating Jira tickets does not mean your product is developer friendly!)
Third, the rise of CSPMs like Wiz has shown the magnitude of cloud and data misconfigurations, but how do we stop misconfigurations from happening in the first place? Products in this area have to embed themselves in the developer workflow, which is tough because most developers are not actively searching for security software. One strategy is to target a specific DevOps pain point, like package management, code merging, or IaC drift, and monetize the security benefits via the security team.
There are a few companies operating at the intersection of these dynamics that I’m excited about, including Jit, Resourcely, Chainguard, and Socket.
Prediction #2: Phishing will get worse before it gets better.
Generative AI will enable hackers to create new, more destructive forms of malware and phishing schemes much faster than were previously possible. Imagine emails that are perfectly designed to get the unsuspecting user to click on them, or webpages with exactly the right content to resonate with a soon-to-be victim. While OpenAI recently launched a detector, its still fairly inaccurate. We expect new security tools that fight AI with AI, putting up guardrails that coach users towards safer behavior and protect them from malicious content. Such a tool would capture already-budgeted anti-phishing budget and over time, could grow to become the posture management platform for insider risk.
Several AI-first companies are well positioned to lead the charge, including OpenAI, Adept, Abnormal, Material, Tessian, and Savvy.
Prediction #3: Automation helps security productivity SOAR to new heights
Security teams are drowning in visibility, while developers are drowning in tickets. Neither party wants more alerts (aka more problems). Teams need to schedule and execute custom workflows (sometimes no-code, sometimes with code) to automatically handle issues end to end. Coupled with the increasingly technical acumen of security teams, we think these trends point to a renaissance for security automation and orchestration. The disruption will happen along two axes:
First, XDR platforms will start eating more and more of the tasks that SIEMs are reliant upon by correlating data from EDR/MDR, logs, and workflow automation. Snowflake and other data warehouses will play a seminal role as the data storage layer for many modern XDR platforms. (Side note: the modern security data stack is a real thing, and will power far more capable detection and response in the future.)
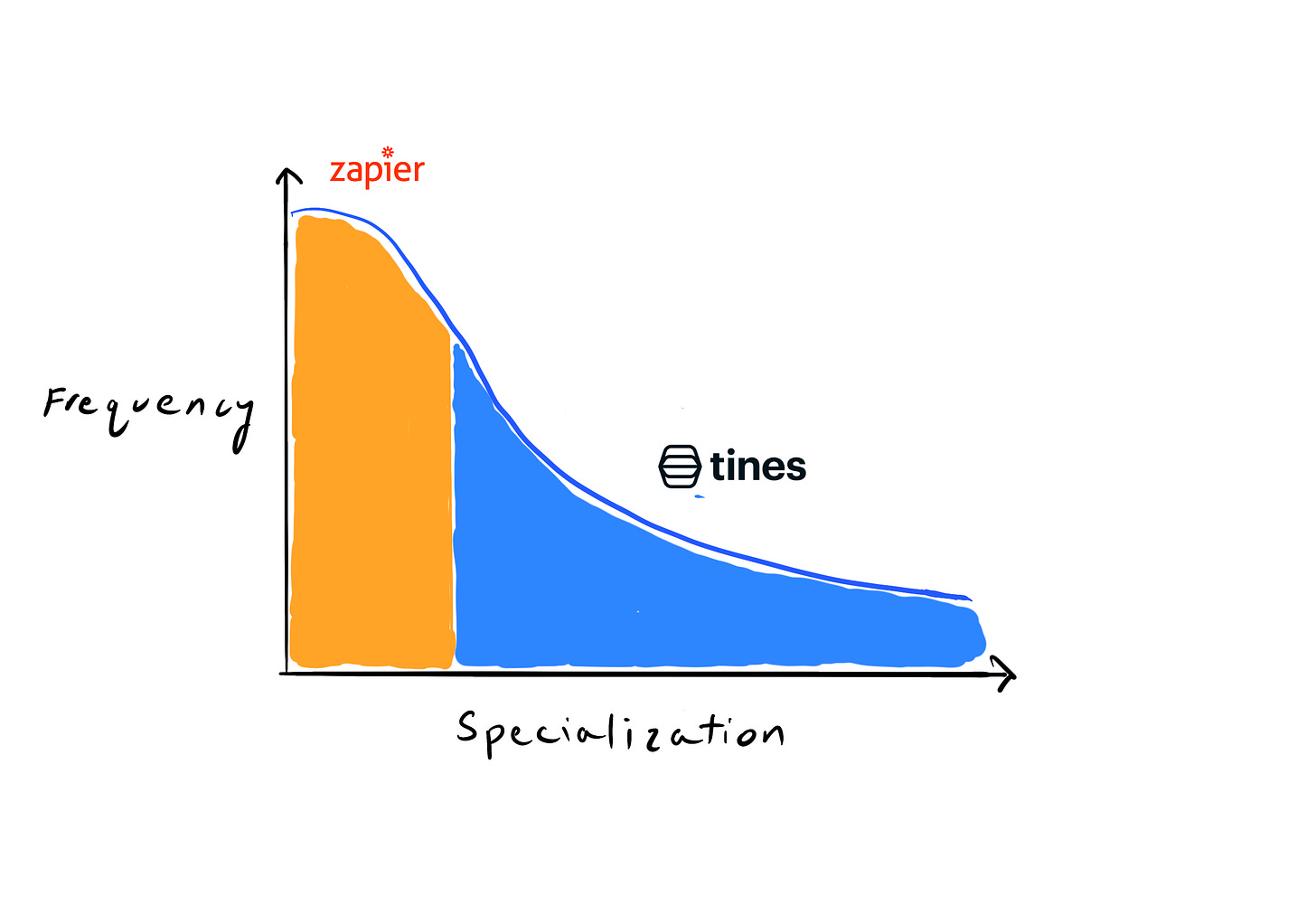
Second, a new breed of SOAR platforms is emerging that offers security a bridge to the rest of the organization. I’ve written before about how automation increases market sizes by enabling new use cases. In security, more user-friendly workflow orchestration products can be adopted by sister teams in IT, Finance, HR, and more, considerably expanding TAM over the prior generation of SOAR. Use cases include just-in-time access reviews (DevSecOps), user de-provisioning (HR, IT, Security), contractor on-boarding (HR, IT, Finance), and more. Mature horizontal tools like Zapier have no incentive to go deep in integrating with the tools that are a nonstarter for security teams, creating an open opportunity.
Some of the companies I’m excited about here include Tines, Torq, Revelstoke, and Hunters.
Personal learnings from the anti-portfolio
Much of this post has been about finding a new attack surface, but it was precisely that sort of thinking that caused me to miss Wiz. (That, and I wasn’t a VC back then, but you know, semantics). In 2022, Wiz became the fastest company ever to go from 0-100m in ARR. Predecessors Evident and Redlock started in 2013 and 2016, respectively, before eventually being combined into Palo Alto Networks’ Prisma platform in 2019.
Wiz, founded in 2020, was not going after a new category. Rather, it was, and continues to be, a refreshingly delightful take on what cloud security could be. Setup was orders of magnitude faster than competitors could muster while alerts that can number in the thousands were thrown out in favor of connected, correlated events that can be easily understood and remediated in real time.
Many security products have the right market in mind, but are hamstrung by product complexity, lengthy set up, and terrible usability. My core learning from Wiz is that experience, usability, and time to value can make the difference. Especially in security.
If this post resonated with you or if you disagree with anything I’ve said, let me know! I’m always happy to talk security at rgarg@baincapital.com





Great article!